NEWS
Our team are happy to share their knowledge through the Hosted blog. Keep checking back for regular updates.
Hosted Blog

By Isaac Gounton
•
September 21, 2022
Migrating Your Company Email to Office 365 the easy, cost effective way. Discover the benefits of migrating your company email to Office 365 with Hosted. Learn how to seamlessly transition to the cloud and enhance collaboration, productivity, and data security. Migrate from Google, Dropbox or Box giving you the peace of mind that all data is in one secure place and easily accessible by all staff.

By Isaac Gounton
•
September 1, 2022
Microsoft has been actively tracking a widespread credential phishing campaign using open redirector links. Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking. Doing so leads to a series of redirections—including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems—before taking the user to a fake sign-in page. This ultimately leads to credential compromise, which opens the user and their organization to other attacks. The use of open redirects in email communications is common among organizations for various reasons. For example, sales and marketing campaigns use this feature to lead customers to a desired landing web page and track click rates and other metrics. However, attackers could abuse open redirects to link to a URL in a trusted domain and embed the eventual final malicious URL as a parameter. Such abuse may prevent users and security solutions from quickly recognizing possible malicious intent. For instance, users trained to hover on links and inspect for malicious artifacts in emails may still see a domain they trust and thus click it. Likewise, traditional email gateway solutions may inadvertently allow emails from this campaign to pass through because their settings have been trained to recognize the primary URL without necessarily checking the malicious parameters hiding in plain sight.
LATEST
SECURITY
CLOUD

By Isaac Gounton
•
September 21, 2022
Migrating Your Company Email to Office 365 the easy, cost effective way. Discover the benefits of migrating your company email to Office 365 with Hosted. Learn how to seamlessly transition to the cloud and enhance collaboration, productivity, and data security. Migrate from Google, Dropbox or Box giving you the peace of mind that all data is in one secure place and easily accessible by all staff.

By Isaac Gounton
•
September 21, 2022
Migrating Your Company Email to Office 365 the easy, cost effective way. Discover the benefits of migrating your company email to Office 365 with Hosted. Learn how to seamlessly transition to the cloud and enhance collaboration, productivity, and data security. Migrate from Google, Dropbox or Box giving you the peace of mind that all data is in one secure place and easily accessible by all staff.

By Isaac Gounton
•
September 1, 2022
Microsoft has been actively tracking a widespread credential phishing campaign using open redirector links. Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking. Doing so leads to a series of redirections—including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems—before taking the user to a fake sign-in page. This ultimately leads to credential compromise, which opens the user and their organization to other attacks. The use of open redirects in email communications is common among organizations for various reasons. For example, sales and marketing campaigns use this feature to lead customers to a desired landing web page and track click rates and other metrics. However, attackers could abuse open redirects to link to a URL in a trusted domain and embed the eventual final malicious URL as a parameter. Such abuse may prevent users and security solutions from quickly recognizing possible malicious intent. For instance, users trained to hover on links and inspect for malicious artifacts in emails may still see a domain they trust and thus click it. Likewise, traditional email gateway solutions may inadvertently allow emails from this campaign to pass through because their settings have been trained to recognize the primary URL without necessarily checking the malicious parameters hiding in plain sight.
By Isaac Gounton
•
August 12, 2022
Ensure a smooth deployment of Windows 365 with Hosted. Understand the technical requirements necessary to leverage the full potential of this cloud-based operating system and empower your workforce. Migrate from Google, Dropbox or Box giving you the peace of mind that all data is in one secure place and easily accessible by all staff.
By Isaac Gounton
•
August 8, 2022
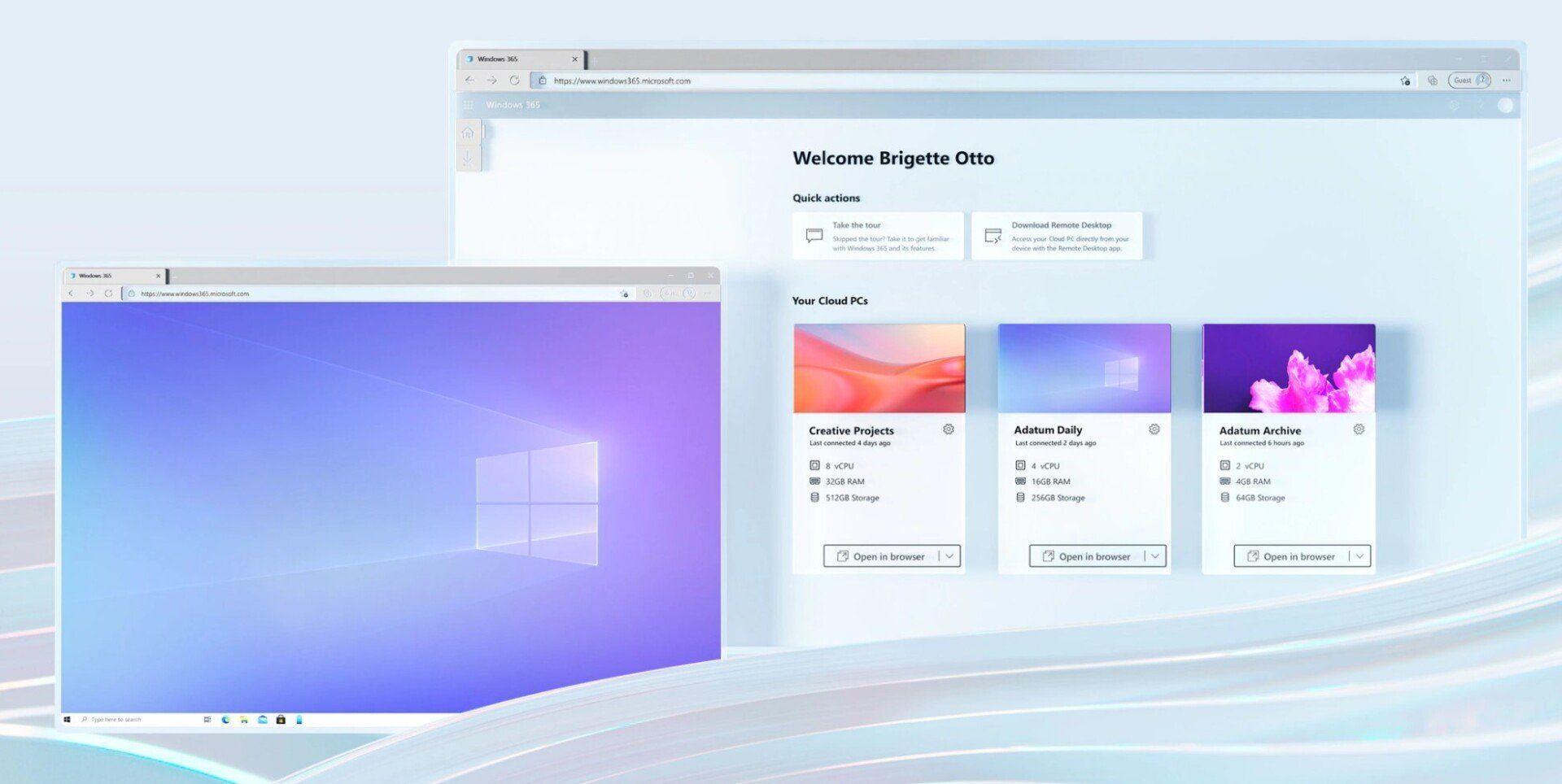
Uncover the power of Windows 365 with Hosted, Explore the innovative cloud-based operating system that delivers a secure and personalized desktop experience anytime, anywhere, on any device. Incorporating Co-Pilot AI to seamlessly read and prompt, simplifying and creating an efficient working practise.